 This is a simple Guide on how to use a RAT. Do not use with malicious intent, only use on consenting individuals for educational purposes only. I will not be held responsible for any damage incurred either to the user or consenting individuals files or computer. Use completely at your own risk. You agree to this statement prior to following this guide.
This is a simple Guide on how to use a RAT. Do not use with malicious intent, only use on consenting individuals for educational purposes only. I will not be held responsible for any damage incurred either to the user or consenting individuals files or computer. Use completely at your own risk. You agree to this statement prior to following this guide.Most AntiVirus products will state that these tools are Trojans (Backdoors) which they are, but the RAT tools can only do what the Hacker (you) wants them to do.
Note: Temporarily Disable your AntiVirus Real-Time Protection and Suspend your Firewall so the Backdoor Trojan RAT won't be detected and so the Client can communicate with the Server.
Go to this site: Sub7legends.com, register and get the latest copy of Sub7 (2.2) and other Misc files if you want. Get the archive password from site, extract archive on your computer. You can use other RAT tools, like BO2K, BOXP, Netbus, Optix, etc but I will be concentrating on the Sub7 RAT.
Process:
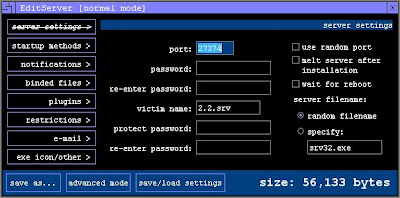
Run Editserver- Normal Mode. Note: Log all settings like Port number, Passwords etc in a text file. When done you can also save all settings to a Preset file. Below are some settings to get you started:
--> Server Settings
Port: 27374
You can set any port number, but Ports 1-1000 are well known ports which are generally used for specific services like SMTP (25), FTP (21) and HTTP (80). So pick a random port over 1000.
Victim Name:
Enter any name you want.
Password:
Enter any Password.
Protection PWD:
Enter any Password.
Melt Server After Installation: Yes
When checked, the Server file, when executed on the remote system will install and then delete itself.
Server Filename: Random
The Server name will be randomly generated.
--> Startup
Reg Key Name: RunDLL32
Leave the default values.
Startup Types:
RegRun, RegRun Services, new method #3 [marklord]. If the Victim has a 9x OS like Win98, use *.ini startup methods.
--> Notifications
email Notification to:
You can be notified by the Server when activated via. ICQ, email, Internet Realy Chat (IRC) and other methods. Below is the format for the email notification:
computer is online on ip: [$ip], port: [$port], password: [$password],
connection: [$connection], server version: [$server_version].
--> Binded Files
Here you can bind the Server to any exe or mp3 files. Depending on your method, the file will either be executed or extracted when the Server is ran. What you can do is use an application or setup file like DVDDecrypter.exe.
--> Plugins
Here you can Bind All x10 Sub7 Plugins, located in the Sub7 2.2\Plugins Folder. You should only use the plugins you need. Eg. the s7keys.dll and s7passwords.dll will log all pressed keys and Passwords on the remote computer, like a keylogger. You can also instruct the server to download the needed plugins when activated from an URL.
--> Restrictions
Here you can limit what the Server can do, usefull if someone else manages to gain control of your remote server.
Here, you can instruct the Server to automaically Email you all pressed Keys, Passwords & Recorded passwords to your email without having to connect to the Server using the Client program.
--> Exe Icon/Other
Here you can set a fake Error message upon remote execution of the Server. Eg. Installation Error: CRC Check Failed. You can also instruct the Server to download additional files from the Web, like more backdoors, etc. You can also set a built-in or external Icon.
--> Done.
You have now built your server. Save the settings to a preset file like: Sub7v2.2-Server-Preset-Setings.s7p. Save the the Server using the 'Save As...' function, if you binded an application, like DVDDecrypter.exe, name your server: DVDDecrypter_[Vir].exe so you can easily recognise the Server.
DO NOT under any circumstances execute the 'server.exe', DVDDecrypter_[Vir].exe or any other servers on your own System.
Note: You can also configure the Server to use a Reverse Connection, effectively this means the Server contacts the Client, so you will not have to know the Victims IP Address. Also, as long as the Firewall (like Windows XP Firewall) is blocking inbound and not outbound connections, it will not block the Server, because the Server initiates the outbound connection to the Client (on your computer) and not Vice-Versa.
You will need some way of getting the Server to the Victim. This guide assumes that the Victim and the Hacker know each other and are following this guide for educational purposes. So, lets assume you have their email address.
Some people will bind their Servers to applications uploaded to file sharing sites, like Rapidshare or P2P networks using Torrent applications and post links to those files on forums, when users download the files onto their computers, the Hacker will be able to connect to those computers. Of course, we won't be doing that.
Rename the DVDDecrypter_[Vir].exe file to DVDDecrypter.exe. Your email and your Victim's email may have AV Scanners (either locally installed AV or WebMail Server AV), if so, commpress the Server (DVDDecrypter.exe) to zip and password protect/encrypt it using Explorer or 7zip so email Scanners won't detect the Virus. You can open zip archive in Explorer> File> Add Password...
Then email the DVDDecrypter.zip containing the Server (only) as an attachment and provide the Victim with the Password for the zip Archive.
You could say in the email that you have found a cool Freeware application for decrypting commercial DVDs to your PC HDD for storage or burning, say its free and that the Victim should definately check it out. You can familarise yourself with the original uninfected app too.
Once the Victim executes the Trojan DVDDecrypter binded Server file, it will run the DVDDecrypter.exe Server. The app (DVDDecrypter.exe) will run while the Server, binded to the app will run and install in the background invisibly simultaneously. Then the server install file will melt (delete itself). The Server is configured to AutoStart with Windows, so should survive PC reboots.
The Victim will not know they have been infected. HIPS (Host Intrusion Protection), up to date AntiVirus and correctly configured Firewalls can interfere with this process.
The Server will send an automated email to the specified email address including the Victims Internet IP Address, Port, Password, connection and server version. Wait x2 days or more for response.
When you receive this email, you can use the client: Sub7 v2.2\Sub7.exe to connect to the Victims PC remotely, using the supplied IP Address (eg. 230.45.95.35), Port (eg. 2737) and PWD obtained from the automated email sent from the Server on the Victims PC.
Note: See txt file: Sub7 v2.2 Server Settings.txt for Configuration (like passwords) if needed.
You now have complete control of the Victims computer, Registry and files. Here are some things you can do:
Take screenshots of computer, log keys, move files to your PC, move files to their PC, delete files, format HDDs, Chat realtime, Browse Files and Registry, Sniff Network, Operate Webcam, Open files, Restart computer,
When you are done go here: Connection> Server Options... to Uninstall the Server from the Victims remote computer. The Client Sub7.exe also has additional features like: IP Tools, Proxy Support and Plugin support.
There are many options in the Client Sub7.exe to control the Victims remote computer using the emailed Server file. Do NOT draw attention to yourself by doing everything you can, this may lead the Victim to become suspicious and install/update their AV or Firewall.
Suppose you wanted to log their Hotmail/MSN/Other passwords, you would go here:
Sub7 Client> Keys/Messages> Keyboard> Open Keylogger... and Open Logged Keys...
--> Usefull applications (Google) >>
ActivePorts, IPScan, Advanced Port Scanner, nPOP, PixaMSN, Remote Shutdown, Remote Desktop Remote Enable, Stealth Tools, UPX Compression, Hex Editor, Sub7 Misc, Tutorials, TCP Ports Info, Gmail SMTP Settings, Sandboxie app.
Disclaimer:
The User 'You' do hearby acknowledge that the auther '[mercnet]' of this guide holds NO responsibility as to what the User may do in regards to this guide. The guide is meant for Educational Use ONLY, consenting users and not for malicious intent. If you do not agree with this statement, then do NOT actively follow this Guide.
Happy hacking!
(c) [mercnet]




No comments:
Post a Comment